Cyber Security
Why is Mobile Security Important & How To Protect Yourself
Mobile devices have become an important part of our lives. We use them to stay connected with friends and family, check the news, and shop for the latest trends. With so much personal information stored on our phones, it’s important to take steps to protect ourselves from mobile security threats. In this blog post, we…
Read MoreHow Often Do You Need a Cybersecurity Audit?
Every year, cyber fraud costs Australian businesses $33 billion dollars. And that’s only the self-reported losses – losses that are unreported could be double this amount. It’s hard to say what is the true cost to the business owner. Leaked customer details, hijacking of websites, stealing client payment information, lack of trust in your business…
Read MoreHow To Prepare for Ransomware Attacks: 5 Questions to Ask Yourself
In 2020, there was a successful ransomware attack every eight minutes. The threat of a ransomware attack is growing more prodigious everyday, and we need to be alert and proactive to protect ourselves from more high-impact attacks. So what questions should you be asking, and what steps can be taken to mitigate the impact of…
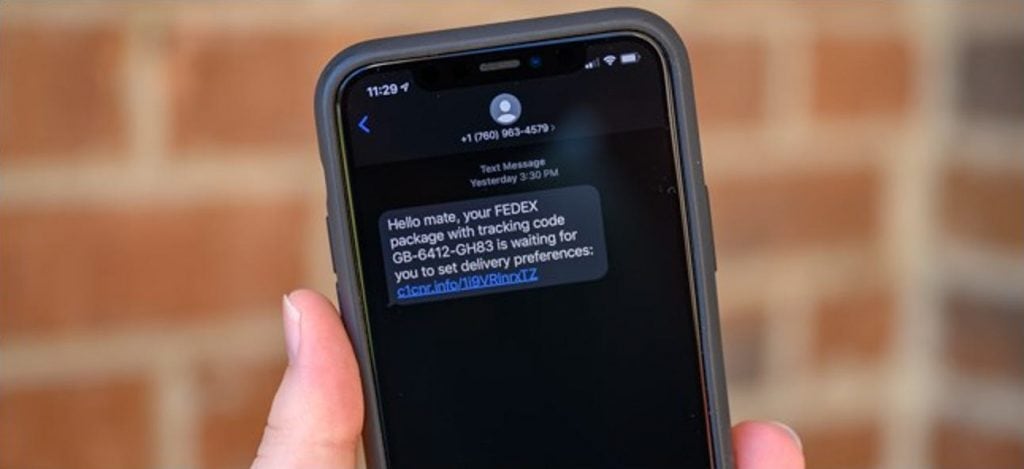
Read MoreScam Text Messages: What Are They & How to Stop Them
Why you’re being inundated with so many scam messages? Australia is rife with conversation about the inundation of scam text messages we have all experienced recently; but why is it happening, and what you can do about it? Some scam text messages are easy to spot, with terrible typos and spelling or obviously fake website…
Read MoreCall Spoofing: How Scammers are Using Fake Phone Numbers to Scam You
There has been a huge increase in ‘Call-Spoofing’ Australia wide in the last few months, but what is it? Why is it happening and what should you do if you receive one? What is Call-Spoofing? ‘Call spoofing’, is the latest weapon used by cyber criminals to encourage people to accept a call. Put simply, Call-Spoofing…
Read MoreTypes of Hackers & How They Attack You
There are so many types of hacks and hackers that it can sometimes feel impossible to keep up, but who are the main culprits and what are they up to? Black Hat Hackers Black hat hackers are known as the ‘bad hackers’; they are motivated by money but often, they just do it for…
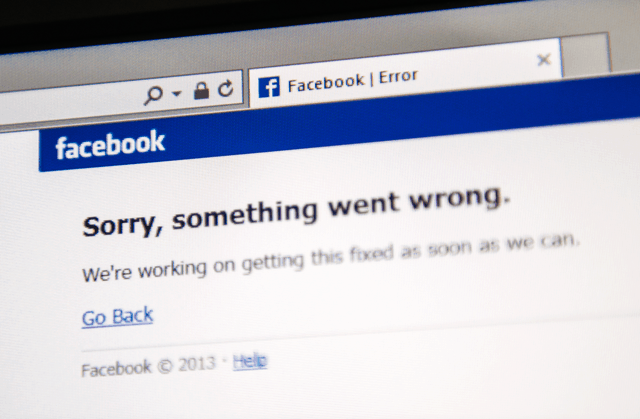
Read MoreFacebook Outage: Technology is Fundamental to the Operation of Most Businesses
The Event Panic struck billions of people on Monday as Facebook, WhatsApp and Instagram all went down at the same time. One thing became very clear, very quickly – the world really relies on these services and the technology industry in general. In a matter of minutes, Facebook had completely disappeared from the internet and…
Read More7 Reasons Why Hackers Hack & How to Prevent It
Why Do Hackers Hack? By the end of 2025, there will be more than 75 billion devices connected to the internet, and every single one of them will be vulnerable to hackers. In 2019 an average of 4,800 websites were compromised each month and we can expect this number to continue to rise; but what…
Read MoreCybersecurity in 2021 & Beyond
Cybersecurity issues have become an increasing day-to-day struggle for businesses, worldwide. Based on recent trends and the side effects of a global pandemic; recent cybersecurity statistics have revealed a huge increase in hacked and breached data from sources that are common in the workplace, such as mobile and Internet of things (IoT) devices. In addition…
Read MoreAre you prepared for the next cyberattack?
There has never been a time when companies and organisations have been more at risk of having their data made public or stolen then through a cyberattack. Prevention is the key to defending against cybercrimes. Using the right technology, the majority of attacks, even the most advanced ones, can be prevented without disrupting the normal…
Read More